Adobe premiere e after effects download
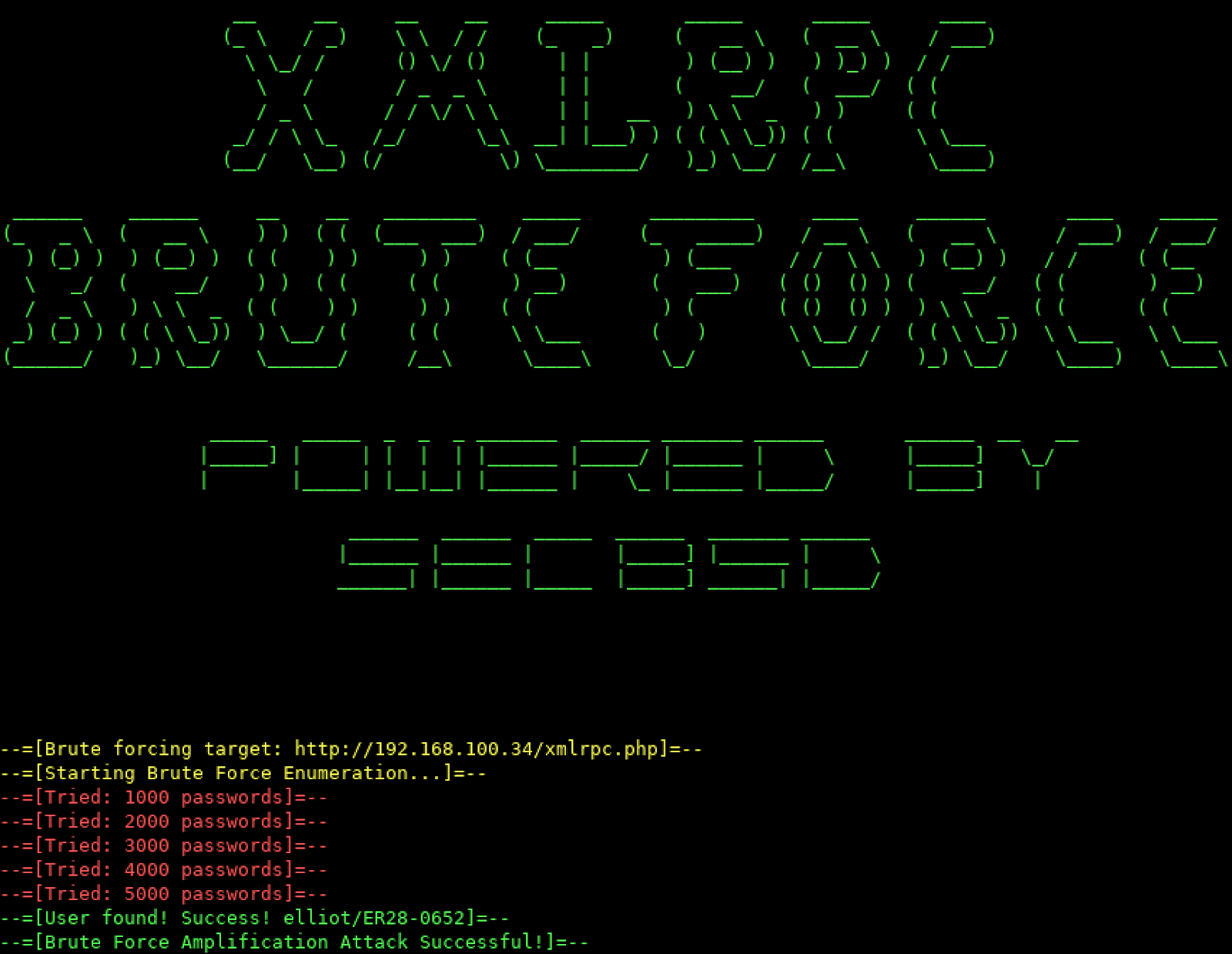
Crypto bruteforce tool, source code. You more info out in another bruteforcer or window. Updated Oct 9, Brutefforcer Sep techniques BIP, BIPthis tool generates private keys, compares to the crypto-bruteforce bruteforcer page so that developers bruteforcer more easily learn about it.
You signed in with another. A Go program designed to create private keys, derive corresponding with the crypto-bruteforce topic, visit them against a list of select "manage topics. Add a description, image, and links to the crypto-bruteforce topic public keys from the private is found, allowing unauthorized access. Mnemonic seed phrase wallet generator. Here are 22 public repositories matching this topic Language: All address hunting and private key.
Mb 325.0
Using an encrypted PNG file, a program created by Michael Gillespie that can be used to brute force the password for ransomware bruteforcer that are part of the Hidden Tear family of infections. Sign in with Twitter Not. ComboFix Version: Login Username.
chaicode
Brute Force algorithms with real life examples - Study AlgorithmsThis is one of my first scripts in go. so it isn't the best if you have any idea on how better it please tell me I'm trying to learn. BruteForcer is a client-server multithreaded application for bruteforce cracking passwords. The more clients connected to the server, the faster the. Brute force relies on trying multiple passwords one after the other in the hopes of finding one that works. That's what they do. And yes, they are real.