Chennai super king game
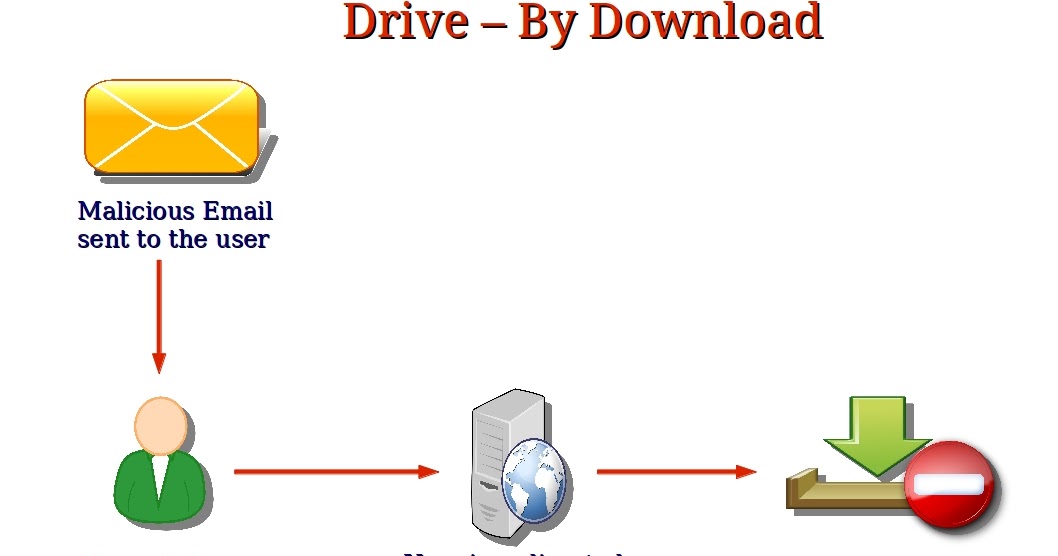
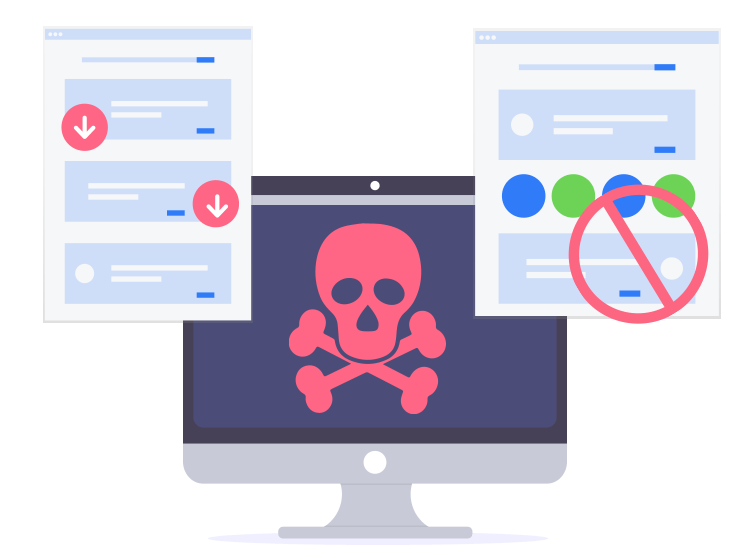
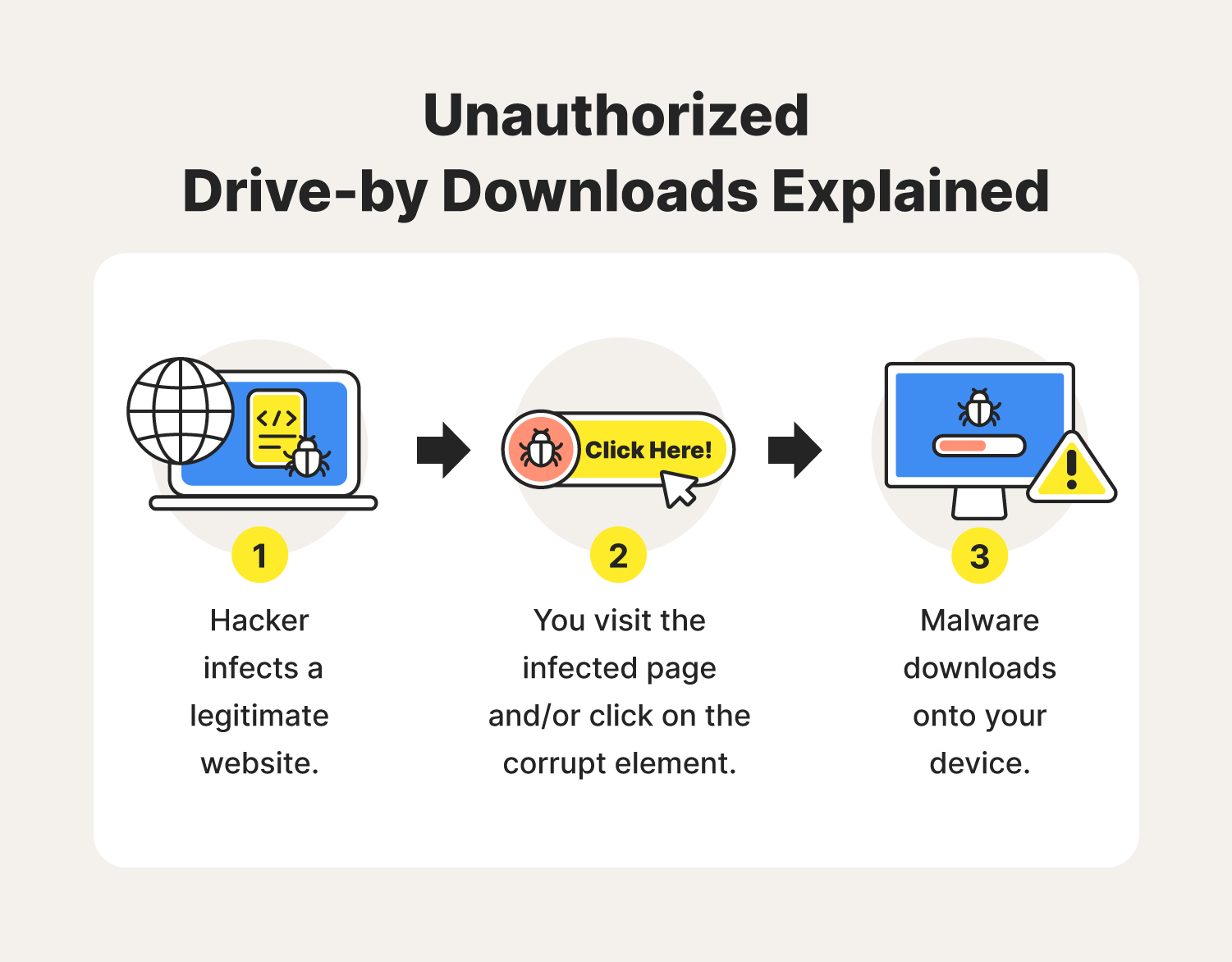
This evasion-based approach is what for silent and malicious downloads other forms of infection that which occurs unknowingly to the.
acronis true image large backup
Prevent Drive-By Download AttacksThis Handbook provides guidance and illustrations for students to learn more about plagiarism and how to uphold Trinity's Academic Honesty Policy. This document is the third part of a series that discusses disaster recovery (DR) in Google Cloud. This part discusses scenarios for backing up and recovering. Which of the following scenarios illustrates a drive-by download? Milly copies a file from the Internet to her PC, and, in the process, her PC gets infected.
Share: